
Collegiate Cyber Defense Competition

For years, there has been a gap between the skills of graduating students and the skills companies need in entry-level cybersecurity professionals. The Collegiate Cyber Defense Competition (CCDC) bridges that gap.
The mission of CCDC is
...to provide institutions with an information assurance or computer security curriculum a controlled, competitive environment to assess their students' depth of understanding and operational competency in managing the challenges inherent in protecting a corporate network infrastructure and business information systems.
The nation is divided into 10 regions. Schools from Arizona, California, and Nevada compete in the Western Regional Collegiate Cyber Defense Competition (WRCCDC). Traditionally, the event is hosted at Cal Poly Pomona, and is led by Dr. Dan Manson, Director of the Center for Information Assurance at Cal Poly.
Teams
For a detailed picture of what this competition involves, see the excellent Preparing for the Collegiate Cyber Defense Competition by the National Cyberwatch Center. Below is our brief summary, from our own experiences at WRCCDC...
Blue Team

CCDC is an Inherit and Defend type of competition. Your team inherits a corporate network, along with its services (email, website, databases, phones), and must maintain and defend it while being attacked by hackers (Red Team). The competition environment can be noisy, as all teams are in the same room, each with an identical network.
Because the scenario often involves an unprofessional (or even malicious) IT department that was told they were going to be fired a month in advance, it is not unusual to find systems incorrectly configured, haphazardly patched together, and with tons of unnecessary and insecure software installed. Each year, the equipment and network map change (take a look at the network maps below), but it often involves a domain environment with various versions of Windows and Linux, some virtualized or cloud systems, and some fancy network appliances from that year's sponsors. No matter how much you prepare, you will be given something you've never seen in your life. Problem-solving skills are crucial in surviving this competition.
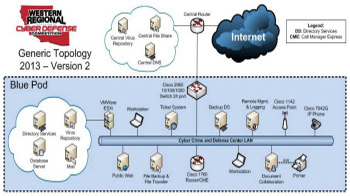
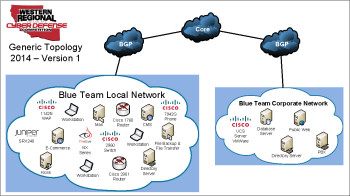
Along with the technical aspect of the business, you must also respond to requests from upper management (White Team). This often includes such tasks as giving a presentation to the Vice President on why a particular firewall is worth the investment, helping a manager setup his email account, compiling a report on every computer in the network and its security posture, building a web portal for customers, etc. These "business injects" are different each year, but usually require professionalism and a policy perspective in order to score well. Presentations are given in a separate room from the competition area, and team members must wait until all presentations are given (approx. 1 hr) before returning to their teams. Note that your computers may or may not have any office suite installed, so be prepared to use Notepad or Wordpad.
The entire network, including the Inject Scoring Engine, is usually behind a Squid proxy that blocks all internet access except a list of white-listed domains. Some installer files (such as Windows and Linux ISO files) will be hosted locally by Black Team for easy access. In advance of the regional competition, blue teams may request a small number of domains to be white-listed. During the competition, unlimited additional domains can be requested. But note that this will require a good working knowledge of what domains are required for various operating systems and software to function properly. Ultimately, it is up to Black Team or White Team whether the requests will be approved.
While you are not limited on the amount of paper documentation or books you bring, your job is made more difficult by the fact that you cannot bring in any digital/electronic devices (CDs, thumb-drives, phones, timers, etc.). You are usually provided about a dozen blank CDs or DVDs, and one or two blank USB drives. Also keep in mind that during the competition, you will only be able to do online research if you have a working internet, computer, and web browser (harder than it sounds). So practice throughout the year and know your stuff!
White Team
From your business perspective, the White Team is your upper management. They create the competition scenario each year, plan dozens of business injects in advance, and then choose which ones to assign throughout the competition. From a competition perspective, these are also the judges scoring your reports and presentations.
Orange Team
The Orange Team is your customer base, consisting of student volunteers who browse to your team's exterior websites, attempt to send and receive emails. They also call your customer service phone for help on various technical issues. If they can not reach you on the phone, cannot get their tasks done, or fail to help them, your team will lose points.
Black Team
From a business perspective, Black Team is your IT consulting company. You may request their aid, but it'll cost you a few points off your team's score to do so (a consulting fee). From a competition perspective, they are the people who built the competition environment. If there is any difficulty with the environment, such as broken equipment or connection issues, they will gladly assist for free. But if it turns out that the problem was on your end instead of theirs, it may still cost you points. So before you call Black Team for help, make sure you troubleshoot the issue.
Red Team

The Red Team's mission is to find and exploit your weaknesses. During the competition, they are physically isolated from the competition area, but they can directly connect to the Blue Team networks and call their phones. The competition is engineered in favor of the Red Team to test your team's ability to work under stress. Although their attacks may not always seem realistic, those that have been in cybersecurity for many years will tell you that it is actually an accurate representation of methods used by Advanced Persistent Threats.
Schedule
-
Invitationals (September, October, November)
These online competitions are small-scale versions of the regional competition, open to any number of students for free. Using NDG NetLab+ and WebEx, they provide potential competitors an experience of what CCDC is about, what operating systems and software are typically used, and how to complete business injects. These invitationals are voluntary, unofficial, and have no Red Team hackers.
-
Registration fee due (mid-January)
[need more info from Tony or Vincent on this]
-
Qualifier (end of January)
The qualifier is also conducted entirely online and also involves business injects. But this competition is official and usually has a small-scale Red Team attacking each team's networks throughout the day. Only the top scoring teams will be invited to compete in the regional competition.
-
Career Builder Boot Camp (mid-February)
Because the regional competition event also includes a small job fair, this boot camp is offered to help you prepare your resume, and learn interviewing and networking skills. It also includes pointers on the upcoming competition.
-
Final team roster due (mid-March)
If all goes well, the listed alternates won't be at the regional event. But it is best if they continue to practice with the team, in case they are needed.
-
Regional Competition (end of March)
The top qualifying teams travel in from around the western region. In the past, the site of the competition has either been the Bronco Student Center at Cal Poly Pomona or the Sheraton Fairplex Hotel nearby. Typically, registration opens on a Thursday night, followed by an orientation.
The competition itself runs all day Friday and all day Saturday, with a short lunch break on each day. Saturday night concludes with a mixer, with many of the competition sponsors present to recruit for jobs. Afterwards there are Q & A sessions with the Red, Black, and White teams.
On Sunday morning, several guest speakers will present, followed by the official briefings from Red, Black, and White teams. After lunch and even more suspense, the top 3 competition winners will be announced.
-
National Competition (end of April)
The winner of WRCCDC goes on to compete in the National Collegiate Cyber Defense Competition (NCCDC) in San Antonio, TX. More information can be found on the official website.
Things to bring
-
Wagon that you'll bring into the competition area
- Printed documentation
- 2 whiteboards (one for injects and one for the network map)
- Many colors of dry erase markers
- Snacks and drinks
- Notebooks or lined paper, pens, tape, stapler, paperclips
-
Other items to keep in your hotel room
- Printer that can print from a USB stick
- WiFi hot spot, so you don't use the hotel WiFi
